Securing the Hybrid or Remote Workforce With SASE
- Home
- Blog Details

- November 17 2021
- admin
Since the transition to hybrid and remote work models began in earnest in 2020, cybercriminals have ramped up their efforts to exploit weaknesses and new vulnerabilities associated with these distributed environments. Surveys and studies have shown that remote workers are often taking shortcuts that circumvent security policies. More than ever, personal devices that may not be configured to meet security requirements are being connected to company resources. Home offices are essentially beyond the control of employers; thus, physical access controls are virtually non-existent. These are a few of the issues companies are struggling with as they strive to provide secure and dependable remote access to their staffers and monitor their work-related activities. Although it was developed before the 2020 workforce transition, the Secure Access Service Edge (SASE) concept seems tailor-made for today’s iteration of the wide-area network.
What is SASE?
The cloud-based SASE service model combines wide area network (WAN) capabilities with security tools including Firewall as a Service (FDAs), Cloud Access Security Broker (CASB), and zero trust access controls that will address and resolve many issues associated with hybrid and remote workforce environments. SASE facilitates secure connections to resources regardless of where they are in relation to those who need access to them. User access controls are based on identity, location, access timeframes, and user device risk assessments. By using what is known as worldwide points of presence, SASE reduces or eliminates latency across what can be a global network.
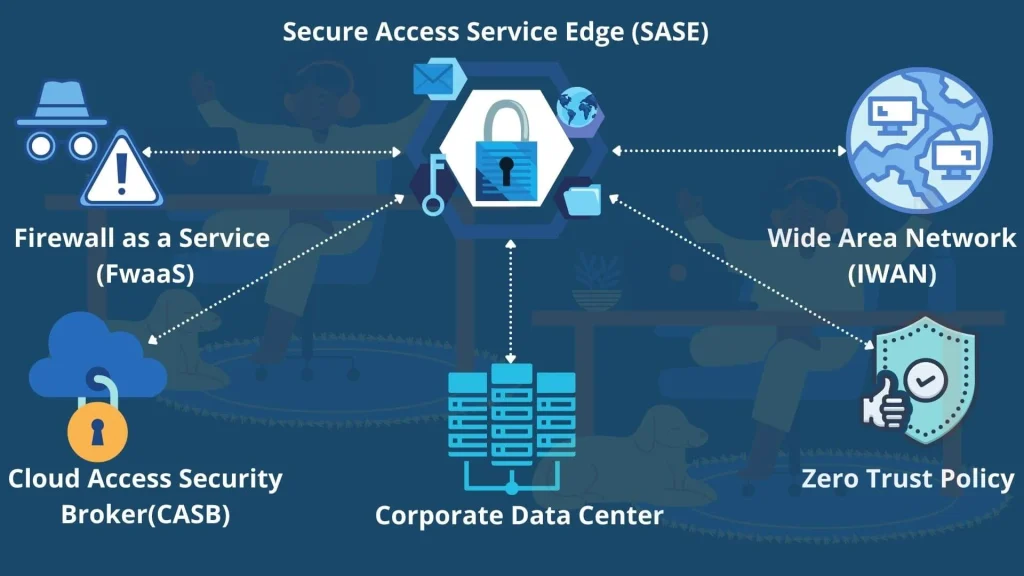
Zero trust is a critical component of SASE. Traditionally, everything and every user within a secured network is afforded at least some level of trust. For example, a user can move about a network accessing resources based on permissions assigned to their account once logged in. However, zero trust emphasizes on “never trust, always verify” principle. Rather than a user signing in once and having the ability to move laterally around the network during that session, both the user and device being used in a zero-trust environment would be required to authenticate each time they attempted to access designated “micro-perimeters” within the network. These micro-perimeters could be encasing applications or services, data, or other assets. Zero trust controls grant access to a micro-perimeter by verifying user identities, devices, request types, locations, activity history, and timestamps. Should a bad actor manage to gain access to a network protected by zero trust controls, they would likely find it impossible to move about and access critical resources.
SASE is highly scalable and flexible. Among others, available security features of SASE may also include data loss prevention, sandboxing, DNS security, and web filtering. Because it is cloud-based, SASE can reduce costs associated with procuring, managing, and maintaining technology resources.
Remote work with SASE
The SASE components discussed thus far serve as examples of how they can benefit organizations whether they are utilizing hybrid, remote, or more traditional work models. There are, however, some SASE advantages that relate more directly to securing and managing remote employees.

SASE facilitates better control over which remote staffers can access applications and websites. It provides more visibility into their access and usage of company resources, thus allowing management to better track those working without direct supervision and ensure that they adhere to policies. The access controls offered by SASE help to lock down home offices by blocking access via unauthorized devices. They prevent the exfiltration of sensitive data and ensure that the absence of organizational control over the physical security of the home office environment does not result in company assets falling into the hands of unauthorized individuals. Additionally, remote workers will connect to company resources via a zero-trust network, thus preventing those resources from being exposed to Internet-based threats.
In closing
Cybercriminals are increasingly targeting remote employees. New threat vectors seem to emerge daily. Remote location and hybrid work models have now become the standard. The recent Covid-19 pandemic is driving an entirely new model of working. SASE not only addresses the threats via its suite of security controls, but it also provides employers with greater insight into and control over the activities of their remote staffers. SASE dramatically reduces the vulnerabilities associated with maintaining a non-traditional WAN that includes numerous sites in the form of home offices where management lacks control over physical access.
While the transition to SASE takes time, especially for an organization currently maintaining its own IT infrastructure, the long-term benefits make it worth the effort, and they may include cost savings as well.

